ONEKEY: Europe’s Most Promising Cybersecurity Start-up
Benefit from instant results and lifetime monitoring.

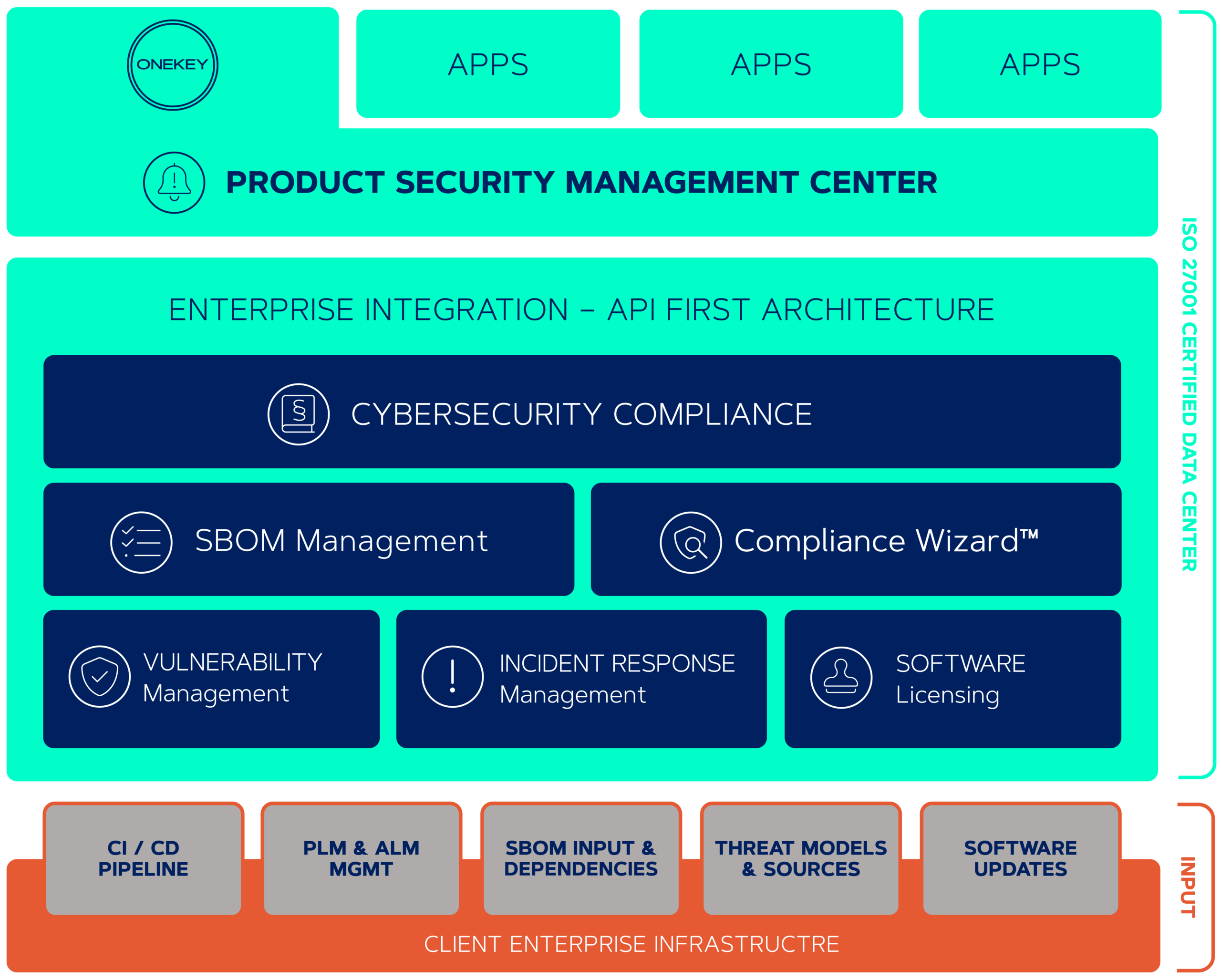
ONEKEY is the leading European Product Cybersecurity & Compliance Platform (PCCP), available worldwide. The platform is developed by world-leading product cybersecurity experts and continuously enhanced.
ONEKEY is available as Software-as-a-Service (SaaS), or on-premise for automated security and compliance analysis and management of connected devices and embedded (IoT/IIoT/OT) products. ONEKEY work with binary code, does not require source code, network or physical access.
Critical vulnerabilities and compliance violations in device firmware are automatically identified and priotised in binary code by AI-based technology in minutes. Proactively audit software supply chains with an integrated software bill of materials (SBOM) generation. “Digital Cyber Twins” enable automated 24/7 post-release cybersecurity monitoring throughout the full product lifecycle.
Integrated compliance checkers enables organisations to check for compliance with many standards and regulations, ie. the upcoming EU Cyber Resilience Act and existing requirements according to IEC62443-4-2, EN303645, UNR155, etc.
The Product Security Incident Response Team (PSIRT) is effectively supported by the integrated automatic prioritisation and mitigation advice for vulnerabilities, significantly reducing the time to remediation.
Implementing complete software supply chain transparency through automated security analysis and compliance checks will substantially support your core mission.
A Software Bill Of Materials (SBOM) lists all software components of a given software. As a producer, it will reduce unscheduled work and avoid components with known vulnerabilities from ending in your products. When choosing or purchasing products, an SBOM will enable a more accurate calculation of total cost of ownership and easier due diligence. As operator, an SBOM will enable you faster identification and resolution of vulnerabilities.
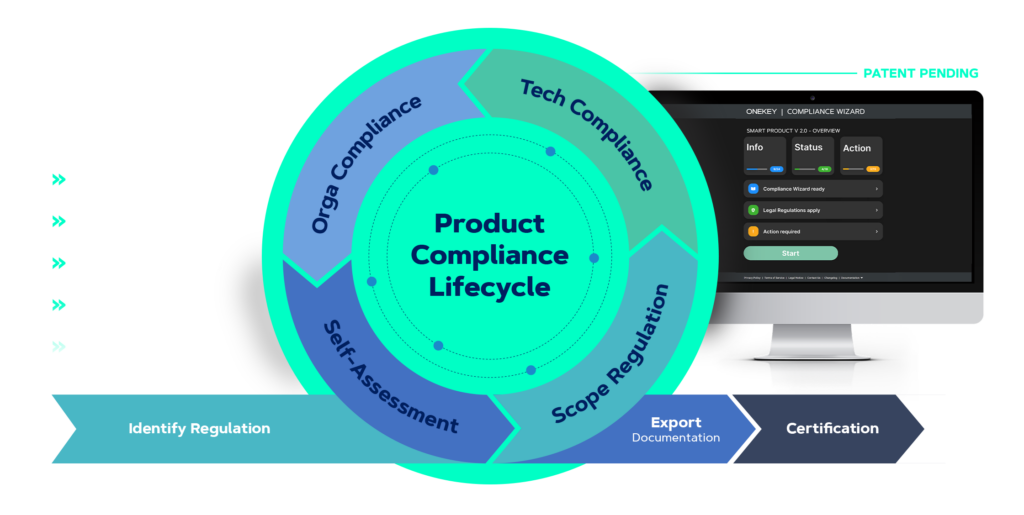
The all new and patent-pending COMPLIANCE WIZARD™ will guide you through the complex journey of your product cybersecurity assessments. A unique combination of automated vulnerability detection, CVE prioritisation, and filtering with a holistic interactive regulation questionnaire will reduce efforts, costs and time of your product cybersecurity compliance process.
Effortlessly navigate the complexities of increasing cybersecurity requirements and risks. The automated solution intuitively guides you through the compliance process, ensuring effective compliance management.
Many cybersecurity standards like the upcoming EU Cyber Resilience Act (CRA) and existing standards like ETSI 303 645, IEC 62443, are already included and its growing each day.
Whether you develop IoT or OT devices yourself or buy them from suppliers,
ONEKEY can automate and maximize your product cybersecurity and
compliance of your connected devices now.
Automated cybersecurity tests and compliance checks.
Early risk detection.
Automatic testing of third-party components.
Ongoing monitoring of previous versions.
Seamless integration into your processes & tools.
Full automation possible.
Lower costs.
With little effort and low costs, you sustainably improve
product cybersecurity in your company, authority or organization.
The ONEKEY firmware analysis platform has been developed as an automated and integrated solution specifically for producers and operators of IoT/OT devices.
We are happy to advise you on the possibilities, benefits, and process integration without obligation.
Book your personal initial consultation NOW – or find out more in the following areas:
We develop/integrate IoT/OT devices for our customers.
We purchase and use IoT/OT devices in our organization.





ONEKEY is a technology-leading European firmware analysis platform available worldwide. The core technology was developed by world-leading pentesting experts and has been continuously enhanced since then.
ONEKEY is available as Software-as-a-Service (SaaS), or on-premise for automated security and compliance analysis of connected devices and embedded systems running IoT/OT firmware. ONEKEY does not require source code, network or physical access.
The platform provides complete supply chain transparency through automated Software Bill Of Materials (SBOM), deep security checks, compliance analysis, and product lifetime monitoring including 24/7 auto-alerting for new vulnerabilities. The ONEKEY firmware analysis platform provides an easy to use web interface and a powerful API that allows for seamless integration with existing tools such as CI/CD, vulnerability management platforms, or ticketing systems.
ONEKEY’s security experts are available for implementation, API integration, and consultation on your current product cybersecurity process.












Click. Fill Form. Download.